Is it possible to crack a password hashed with sha256 with hashcat? [with screenshots]
SHA256 algorithm was invented to generate 256-bit (or 32-byte) hash. They write it will take you several years to crack it. It's true, but there're cases you can brute-force it (for example, with hashcat tool). At least you can try. In this article I'm using openSUSE Linux distro and openCL framework drivers for my NVIDIA GeForce GTX 1060 Mobile graphic card.
Here's an example, how to crack SHA256-hashed password in several minutes using haschat tool.
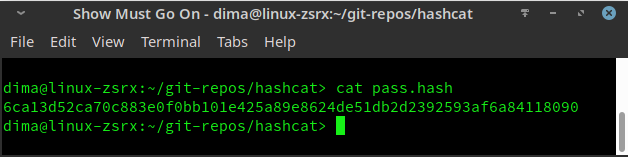
Let's take a hash of a password, stored in pass.hash file:
$ cat pass.hash
In case we want use hashcat to brute-force, let's read, what is written in help file (or man). If you are new to linux, remember, that reading --help and man files is very important thing while working in linux.
What we are looking for? Our goal is brute-force attack and our victim is a password hashed with SHA256 algorithm:
-a, --attack-mode
and then ..
# | Mode
===+======
0 | Straight
1 | Combination
3 | Brute-force
6 | Hybrid Wordlist + Mask
7 | Hybrid Mask + Wordlist
Ok, now we know we have to use -a3 flag. Good. Let's find, what we have to do to crack sha256 hashed file..
-m, --hash-type
Great, -m parameter for hash-type. Our hash-type is SHA256. Let's read more...
1400 | SHA-256 | Raw Hash
Now, let's contruct a command to brute-force our sha256 hashed password:
$ sudo ./hashcat -m 1400 -a 3 pass.hash
and result?
6ca13d52ca70c883e0f0bb101e425a89e8624de51db2d2392593af6a84118090:abc123
Session..........: hashcat
Status...........: Cracked
Hash.Name........: SHA2-256
Hash.Target......: 6ca13d52ca70c883e0f0bb101e425a89e8624de51db2d239259...118090
Time.Started.....: Wed May 6 21:40:58 2020 (0 secs)
Time.Estimated...: Wed May 6 21:40:58 2020 (0 secs)
Guess.Mask.......: ?1?2?2?2?2?2 [6]
Guess.Charset....: -1 ?l?d?u, -2 ?l?d, -3 ?l?d*!$@_, -4 Undefined
Guess.Queue......: 6/15 (40.00%)
Speed.#1.........: 1053.0 MH/s (9.61ms) @ Accel:4 Loops:256 Thr:1024 Vec:1
Recovered........: 1/1 (100.00%) Digests
Progress.........: 20971520/3748902912 (0.56%)
Rejected.........: 0/20971520 (0.00%)
Restore.Point....: 0/1679616 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:256-512 Iteration:0-256
Candidates.#1....: lunier -> hshc56
Hardware.Mon.#1..: Temp: 57c Util: 95% Core:1657MHz Mem:3802MHz Bus:16
Started: Wed May 6 21:40:54 2020
Stopped: Wed May 6 21:40:59 2020
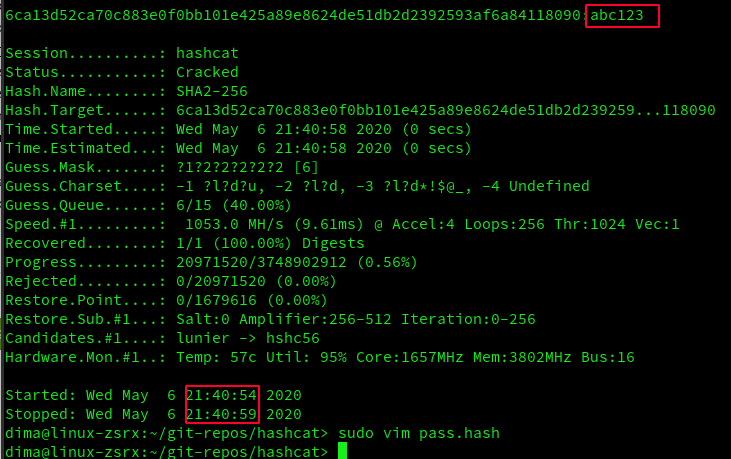
Password was cracked in 5 seconds and it's abc123.
Conclusion
In our model case password was generated by me and it was .. very simple, as you see. Password like abc123 is crackable within several seconds even hashed with SHA256 algorithm. I think you see clearly on a real example, what it means to have so simple password (very short, only small letters and digits, no capitals, no special symbols).
Next time, think a little bit more about security and passwords you choose.