Atom installation on openSUSE Linux: Signature verification failed error resolution
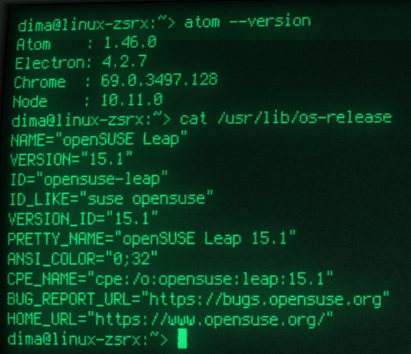
Atom is a very popular "hackable text editor for the 21st Century" not only for linux, but owners of openSUSE Linux can have problems with unsigned package while installing an .rpm package:
Error: INVALID:atom-1.46.0-0.1.x86_64(file-eca764a8): Signature verification failed [6-File is unsigned]
If you still want to install it on your openSUSE system, there's a problem resolution:
- Go to
/etc/zypp - Open file
zypp.conf(as a root) and find a line# pkg_gpgcheck = unset -> according to gpgcheck.Leave this line without change :D - Add following line above:
pkg_gpgcheck = off - Save file and exit.
- Install Atom .rpm package one more time. It will go without a problem.
Following this operation will switch off package signature verification and you will be able to install Atom.
Important notice
Problem with unsigned package was added to issues on official Atom github repository several years ago, but developers still didn't resolve it. Please, take this information with understanding, that Atom is being developed by a group of people, who have programmed very popular and really great text editor for several programming languages and platforms totally free.